The operating system I often work with is windows 7, and to ensure greater safety, I installed Kaspersky Internet Security antivirus software. One day, looking through one of the web pages, I noticed a very interesting code, which in my opinion should not have been on the page.
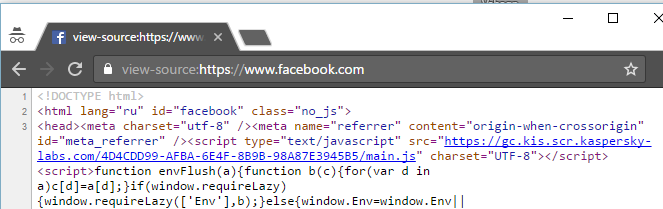
Why does Facebook use javascript code with Kaspersky website?. I immediately realized that my antivirus made MITM traffic (http & https), and injected its code to track the activity on the page. Hmmm, why not create a special page that will monitor the Javascript's scripts, and understand - have on the client computer any antivirus, include KIS.
Create on the server first page - iframe.html
<!DOCTYPE html>
<html lang="en">
<head/>
<img src=x />
<script type="text/javascript" />
</html>
and after create second page - index.html with this HTML code
<!DOCTYPE html>
<html>
<head>
<title>Remotely AV detection</title>
</head>
<body>
<iframe style="width:10px; height:10px; display:block; visibility:show" id="frmin" src="/iframe.html"></iframe>
<button onclick="myFunction()">Check AV</button>
<script>
function myFunction() {
var frm = document.getElementById("frmin");
ka = frm.contentDocument.getElementsByTagName('html')[0].outerHTML;
if (ka.indexOf("kasperskylab_antibanner") !== -1)
{
alert("AV name is Kaspersky");
}
}
</script>
</body>
</html>
When we open index.html page, it will load iframe.html and inject JS code. In this img we can see changed iframe page code
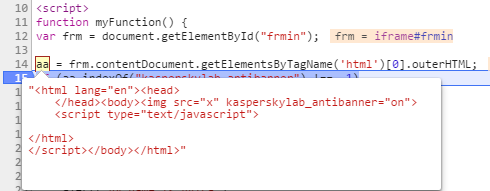
great, to detect, KIS antivirus needs to get code from iframe.html page and parse strings, if the page has kasperskylab_antibanner then we can say - the client computer has installed KIS antivirus.
I wanted to see how things will pan out from other antivirus software if other anti-virus software to detect, or only KIS. Next, consider Avira, Norton, DrWeb antivirus, if anyone wants to continue this mini study, I will be glad to hear about the rest of it works.
Antivirus Avira, Norton, DrWeb, together with the installation of the system, for the chrome browser, install and even add-ons which are as of injectate to the page specific data which can be Oh detectit.
Dr.Web
Product version DrWeb Security Space 11.0
Chrome extension name s - Dr.Web Anti-Virus Link Checker Extension URL
https://chrome.google.com/webstore/detail/drweb-anti-virus-link-che/aleggpabliehgbeagmfhnodcijcmbonb?hl=en-US On the index.html page injected follow code
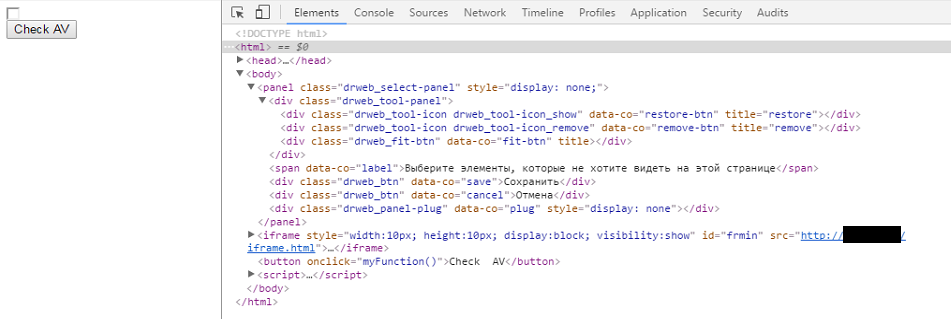
i.e. using the following simple JS code can be found installed DrWeb us or not.
<script>
if (document.getElementsByClassName('drweb_btn').length > 0)
{
alert("AV name is DrWeb");
}
</script>
Avira
When installing Avira antivirus Pro, it installed 2 extensions in the Chrome browser Avira Browser Safety and Avira Save Search Plus
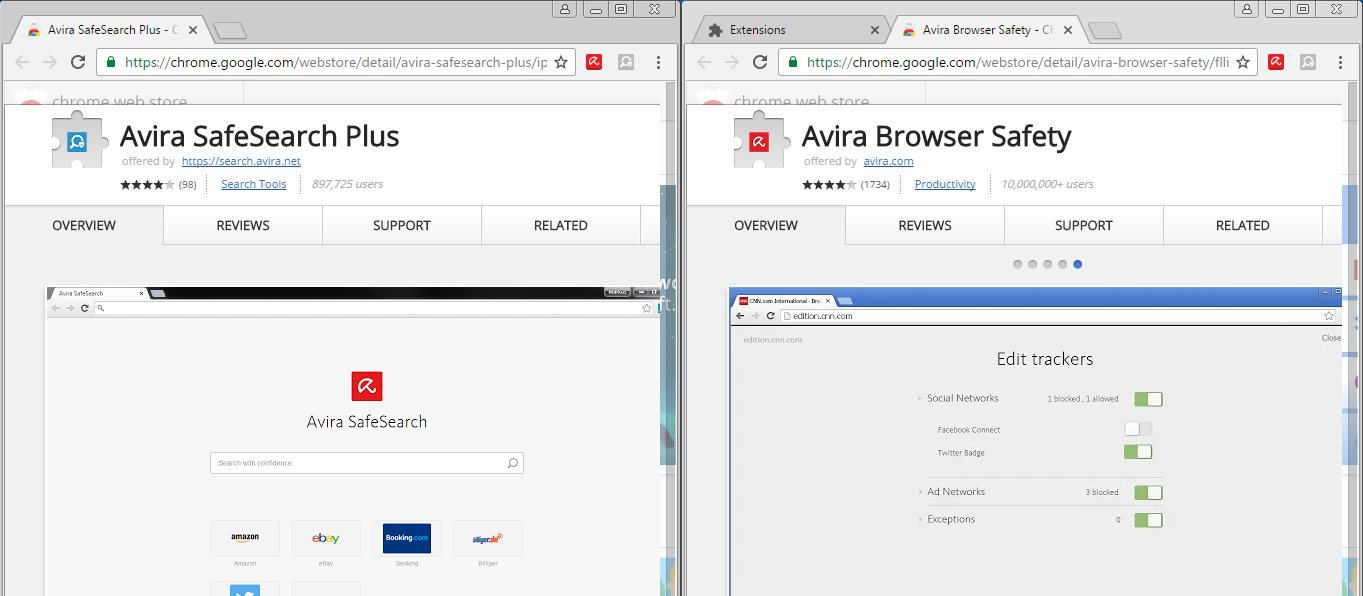
Avira on the page index.html injected iframe which has the following form
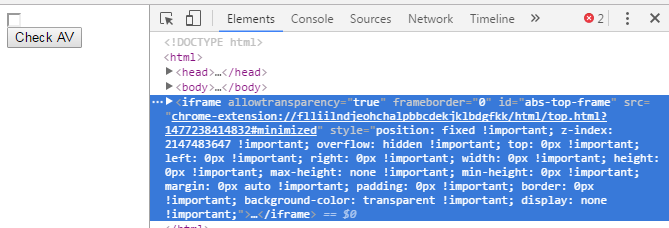
and it turns out JS code for detect Avira extension is as follows
var AV = document.getElementById("abs-top-frame")
if (AV!==null)
{
if (
AV.outerHTML.indexOf('/html/top.html')>=0 & AV.outerHTML.indexOf('chrome-extension://')>=0
)
{
alert("AV name is Avira");
}
}
Norton
And finally the last extension to AV which I had to consider - Norton He has installed, like Avira, 2 extension
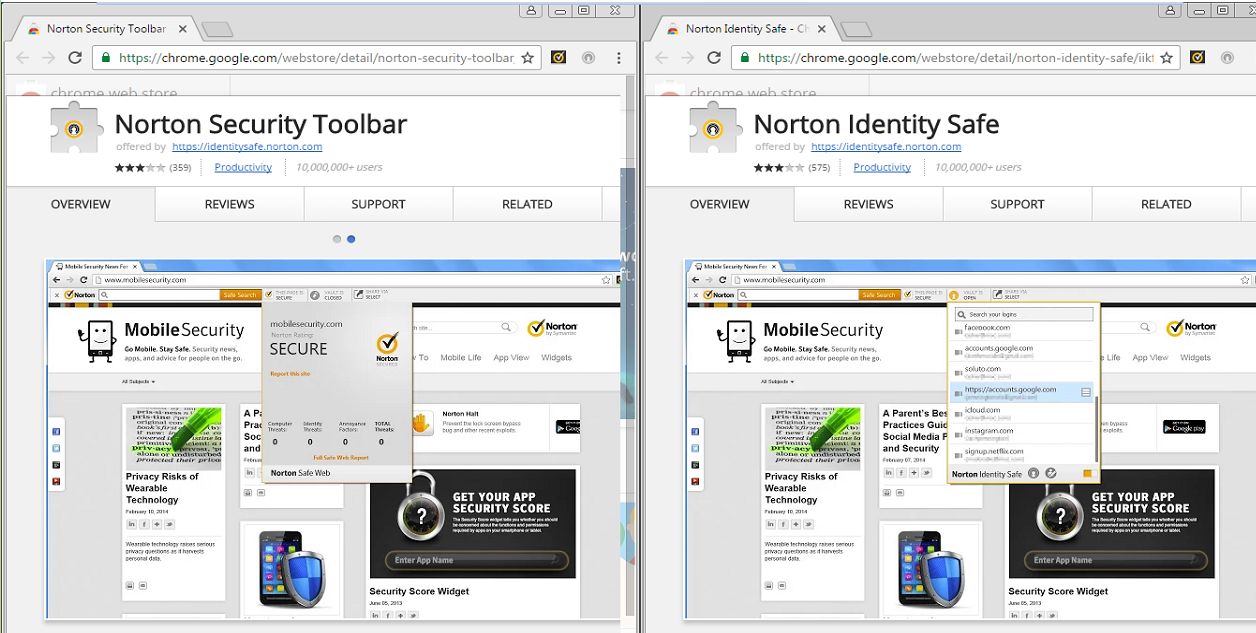
JS code which is implemented by the extension on the page as follows
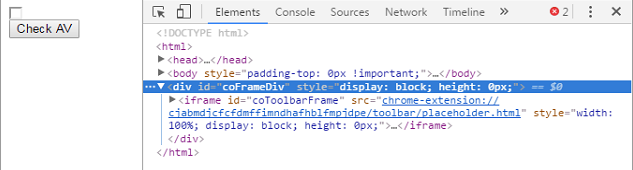
and in the end, it turned out that it is also very easy to detected using this JS code
var NAV = document.getElementById('coFrameDiv');
if ( NAV !== null)
{
var nort = NAV.outerHTML;
if (nort.indexOf('coToolbarFrame')>=0 & nort.indexOf('/toolbar/placeholder.html')>=0 & nort.indexOf('chrome-extension://')>=0 )
{
alert("AV name is Norton");
}
}
Conclusion
- This method does not guarantee 100% detection AV, as it is based on verification of the installed anti-virus extension for Chrome which can be disabled by the user.
- The main idea for the writing of this mini article came after reading this article remote-detection-of-users-av-via-flash
- Code of this project can found AVDetection